In today’s digital world, where cyber threats have become increasingly advanced and persistent, strong network security is crucial. During my internship at Hitachi Vantara Federal, I worked on a project applying machine learning techniques to enhance intrusion detection systems (IDS) using the CICIDS 2017 dataset and the Pentaho+ DataOps Platform. The focus was on distinguishing between regular network traffic and potential threats such as DDoS and port scanning attacks, utilizing XGBoost and Principal Component Analysis (PCA) for dimensionality reduction.
Intrusion detection is a vital aspect of network security, aimed at identifying malicious activities and unauthorized access. Traditional IDS approaches often face challenges with high false-positive rates and difficulty adapting to evolving threats. By leveraging machine learning, we were able to develop more accurate and adaptable models that effectively differentiated between normal and malicious traffic patterns.
What is XGBoost?
XGBoost, which stands for eXtreme Gradient Boosting, is a powerful machine learning algorithm known for its speed and precision. Its ability to handle large datasets and uncover complex patterns makes it particularly well-suited for intrusion detection.
Key Features of XGBoost:
- Efficiency: Utilizes parallel processing and tree pruning to speed up model training and improve performance.
- Flexibility: Supports various data types and can be tuned with hyperparameters to suit specific needs.
- Accuracy: Consistently outperforms many other algorithms in classification tasks due to its ability to capture complex interactions between features.
Using PCA for Dimensionality Reduction
Network traffic data is often high-dimensional, making it difficult to visualize effectively. To overcome this challenge, I used Principal Component Analysis (PCA) to reduce the number of features while preserving the key variations in the data. This approach simplifies the dataset and allows for two-dimensional visualizations that offer clear insights into data distribution and model performance.
- Dimensionality Reduction: PCA condenses the dataset into two key components (PCA1 and PCA2), streamlining the data without losing essential information.
- Visualization: This reduction makes it possible to plot data on a 2D graph, helping to identify patterns and distinguish between benign and malicious traffic.
- Model Evaluation: It also allows us to visualize decision boundaries, making it easier to assess how well the model separates different types of traffic.
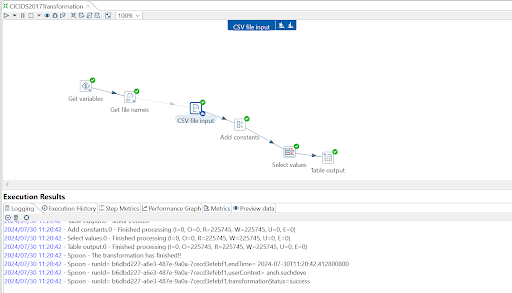
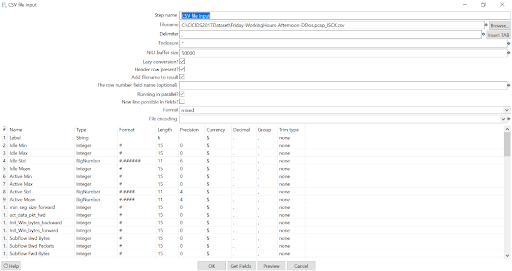
Pentaho+ Exploration
Using the CICIDS 2017 dataset, I built and trained an XGBoost model to classify network traffic as either benign or malicious (DDoS or port scan attacks). The process involved several Pentaho Data Integration steps, including data preprocessing, feature engineering, and applying PCA for dimensionality reduction. The PCA-transformed data provided a clear visual representation of how the model distinguishes between these classes.
Key Takeaways
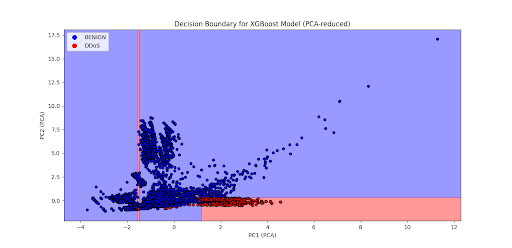
Decision Boundaries: Visualizing the model’s decision boundaries on the PCA plot highlighted the areas where it predicts different classes, allowing us to evaluate its accuracy and spot any overlaps.
Performance Metrics: The model performed well, achieving high accuracy, precision, and recall, demonstrating its ability to effectively identify cyber threats.
- Improved Threat Detection
-
- Adaptive Models: Machine learning models that adjust to evolving threats provide continuous protection against new attack methods.
- Reduced False Positives: More precise classification reduces unnecessary alerts, easing the workload for security teams
- Better Visualization
- Actionable Insights: Visual tools help security analysts quickly detect patterns and trends in network traffic, improving decision-making.
- Model Transparency: Clear visuals of decision boundaries and data distribution make the model easier to interpret and build trust.
- Strategic Advantage
-
- Advanced Technology: Using state-of-the-art machine learning enhances Hitachi Vantara Federal’s standing as a leader in network security.
-
Tailored Solutions: Customizable models that adapt to specific client requirements strengthen the company’s service offerings.
Conclusion
Using XGBoost and PCA for intrusion detection marks meaningful progress in strengthening network security. As cyber threats become more sophisticated, leveraging advanced machine learning is key to staying one step ahead. This project not only demonstrates the power of these technologies but also underscores the strategic benefits they offer to Hitachi Vantara Federal and its clients.
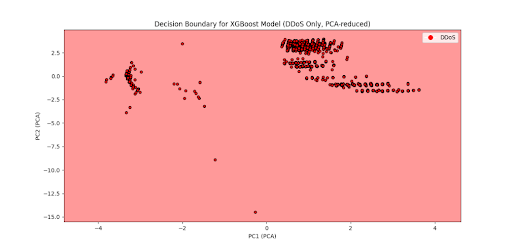
Final Models

This blog post was authored by Ansh Suchdeve as part of Hitachi Vantara Federal’s Pentaho+ Data Science 2024 summer internship program.


